Learning the friendly way
Dive into our resources, guides, and articles for all things money-related. Grow your financial confidence with our experts curated tips and articles for both experienced and new investors.
LATEST ARTICLEs

In today's digital-first economy, businesses across all sectors are seeking innovative financial solutions to drive efficiency, enhance customer experiences, and unlock new revenue streams. One compelling strategy is the implementation of co-branded credit cards, which have been shown to significantly boost customer loyalty and spending.
Notably, 75% of financially stable consumers prefer co-branded cards for their rewards and benefits, indicating a strong alignment between these card programs and consumer desires.
By collaborating with financial institutions to offer co-branded cards, businesses can create tailored payment solutions that meet customer expectations and reinforce brand loyalty. This approach transforms the payment infrastructure from a mere operational necessity into a strategic asset that fuels growth.
For instance, the co-branded credit card market is projected to grow from $13.41 billion in 2023 to $25.72 billion by 2030, reflecting a compound annual growth rate (CAGR) of 9.74%.
Whether you're in retail, SaaS, or manufacturing, a tailored card program could be the key to transforming how your business engages with customers—and how you scale.
What is card program management?
Card program management encompasses the end-to-end process of designing, implementing, and optimising payment card solutions tailored to your business. From corporate expense cards that streamline internal processes to branded payment cards that enhance customer loyalty, these programs offer versatility that can benefit virtually any organisation looking to modernise its financial operations.
As businesses continue to navigate increasingly complex markets, those equipped with flexible financial tools gain a significant competitive advantage. The right card program doesn't just process payments—it generates valuable data, reduces administrative burden, and creates opportunities for deeper engagement with both employees and customers.
Why it matters
At its core, card program management involves overseeing all aspects of a payment card ecosystem—from issuing and distribution to transaction processing, reporting, and compliance. Modern card program management platforms provide businesses with the infrastructure to create customised payment solutions while maintaining visibility and control.
This matters because traditional payment methods often create friction points that slow business growth. Manual expense reporting, limited payment visibility, and rigid financial systems can drain resources and limit innovation.
However, a well-managed card program addresses these pain points by automating processes, enhancing security, and providing greater flexibility.
Key benefits for businesses across sectors
Streamlined operations
Card programs dramatically reduce administrative overhead by automating expense tracking, simplifying reconciliation, and eliminating paper-based processes. This operational efficiency translates directly to cost savings and allows your team to focus on strategic initiatives rather than transaction management.
Enhanced Customer Experience
For businesses that implement customer-facing card programs, the benefits extend to experience enhancement. Branded payment cards can strengthen loyalty, while instant issuance capabilities meet modern expectations for immediacy.
From hospitality to healthcare, organisations are using card programs to differentiate their service offerings.
Data-driven insights
Perhaps the most overlooked advantage of modern card program management is the wealth of data it generates. Every transaction becomes a data point that can inform business decisions, reveal spending patterns, and identify opportunities for optimisation. This business intelligence becomes increasingly valuable as programs scale.
Scalability and flexibility
As your business grows, your card program can evolve alongside it. Whether you're expanding into new markets or adding new product lines, a well-designed card program adapts to changing requirements without requiring complete system overhauls.
The implementation process simplified
Implementing a card program doesn't have to be overwhelming. The process typically follows these key steps:
- Assessment and strategy development: Evaluate your current payment ecosystem and define clear objectives for your card program.
- Platform selection and integration: Choose a card program management solution that aligns with your technical requirements and business goals, then integrate it with your existing systems.
- Program launch and optimisation: Deploy your program with proper training and support, then continuously refine based on performance data and user feedback.
Real-World Impact
Across industries, businesses are leveraging card program management to solve specific challenges:
- Retail companies are implementing instant digital card issuance to capture sales opportunities.
- Healthcare providers are using specialised payment cards to simplify patient financial assistance.
- Manufacturing firms are deploying corporate card programs with custom spending controls to streamline procurement.
The common thread? Each organisation is using card program management as a strategic tool rather than just a payment method.
How Tap can help
Navigating the complexities of card program management requires expertise and the right technology partner. Tap's comprehensive platform brings together cutting-edge technology with industry-specific knowledge to help businesses design, implement, and optimise card programs that deliver measurable results.
Our solution addresses common challenges like regulatory compliance, security concerns, and integration complexities, allowing you to focus on the strategic benefits rather than implementation hurdles.
Ready to explore how card program management could transform your business operations and drive growth? Connect with Tap's team of specialists for a personalised consultation and discover the potential of a tailored card program for your organisation.
Article Framework: Card Program Management
Tone & Perspective
- Tone: Professional, informative, and authoritative.
- Perspective: Written from an expert viewpoint, educating businesses on launching and managing a successful card program.
Priority Headings & Structure
1. Introduction
- What is card program management?
- Why businesses need effective card program management.
- Overview of key stakeholders (issuers, networks, processors, etc.).
2. How Card Program Management Works
- Key components: issuing, processing, compliance, and risk management.
- The role of a program manager (self-managed vs. outsourced).
- The relationship between issuing banks, networks, and program managers.
3. Core Elements of a Successful Card Program
- Program Design: Choosing card types (prepaid, debit, credit), network selection (Visa, Mastercard), and branding.
- Issuance & Account Management: BIN sponsorship, account setup, and customer onboarding.
- Compliance & Risk Management: KYC, AML, PCI DSS, and fraud prevention strategies.
- Transaction Processing & Settlement: How funds flow through the ecosystem.
- Customer Experience & Support: Ensuring smooth cardholder interactions.
4. Self-Managed vs. Partner-Managed Card Programs
- Benefits and challenges of managing in-house.
- When outsourcing makes sense.
- How third-party program managers add value.
5. Key Considerations Before Launching a Card Program
- Business goals and revenue model.
- Regulatory and security requirements.
- Time-to-market considerations.
6. Trends & Future of Card Program Management
- Embedded finance & BaaS (Banking-as-a-Service).
- AI-driven fraud detection and risk management.
- Open banking and API-driven solutions.
7. Conclusion & Next Steps
- Recap of key insights.
- How businesses can get started with a card program.
- Contact a program management expert.

Got some exciting news, Card Auto Top-Up is finally here, and it’s about to make your life way easier.
Say goodbye to those "uh-oh" moments at checkout. This feature automatically tops up your card when your balance gets low, on your terms, no surprises.
You asked, we delivered. We took your feedback and built Auto Top-Up to take the stress out of managing your spending. Your card stays ready to go, so you can focus on more important things (like deciding what to order for lunch).
And here’s the cherry on top 🍒, you can now use your crypto for payments! Pick any of your crypto holdings, top up your card, and start spending—simple as that.
Let’s break it down and show you why Auto Top-Up is about to be your new favorite feature.
No More "Oops, My Balance!" Moments 🙀
We've all been there, your card balance runs low right when you need it most. Auto Top-Up has your back.
Set It and Forget It
Activate it once, and you're good to go. No more scrambling to manually top up your card every time funds run low.
Your Money, Your Rules 💸
Prefer fiat? Crypto? A mix of both? Auto Top-Up lets you choose what works best for you.
Always Ready to Spend
With Auto Top-Up, your card stays funded, so you’re always ready to pay, no interruptions, no stress.
How it works? ✨
With Auto Top-Up, you're in complete control. You decide:
- The minimum balance that triggers an automatic reload amount.
- How much to add when your balance dips below your set threshold.
- Which currency you want to use.
Imagine you're about to make an important purchase, only to realise your card balance is too low. Frustrating, right? Those days are over.
Set your minimum balance to threshold, and Tap will automatically reload your card before you ever hit zero, using your preferred currency.
Ready to make your life easier? Enabling Auto Top-Up is quick and easy:
- Log in to your account.
- Navigate to your card settings.
- Enable Auto Top-Up and customize your preferences.
- Enjoy your card!
Built for peace of mind 😌
Auto Top-Up takes the hassle out of managing your card. Whether you’re travelling, shopping online, or covering everyday expenses, your Tap card will always have your back when you need it.
Ready to get started?
Make sure your Tap app is up to date to start using the new Auto Top-Up feature, and then follow the flow within the Card section.
Got any questions about Auto Top-Up? Our support team is ready to help you get started.

There’s no denying that the recent surge in Bitcoin adoption has largely been fueled by the incredible bull run. With mainstream media, large corporations, and more retail investors taking notice, many merchants have followed suit and added the original cryptocurrency to their list of payment options. As the market erupts, let’s explore what can you buy with Bitcoin exactly.
Bitcoin’s Surge In Adoption
While 2020 was a challenge for most industries, the crypto markets saw unbelievable gains. Despite the universal market destruction that was witnessed across the board, Bitcoin flourished from $3,870 in March to an all time high of $20,000 by the end of the year. Just one week into the new year and the cryptocurrency had doubled reaching $41,515. By 21 February the cryptocurrency was worth $58,330, almost triple the previous all time high.
The extended bull run was due to large firms moving their company reserves from fiat to BTC, with Tesla bringing a lot of media attention to both this pattern but Bitcoin in general. As more people sought to enter the market, more vendors, businesses and retailers sought to offer it as an alternative payment option. According to a study conducted by HSB in 2020, 36% of small-medium businesses in the US accept Bitcoin. This is also likely to triple in coming months.
What Can You Buy With Bitcoin?
As you’ll see below, almost everything. While not every store offers Bitcoin payments, there are plenty of services which offer gift cards for such stores that can be bought with BTC. Where there’s a will, there’s a way. Let’s dive into all the things available for purchase with Bitcoin. To make things a bit simpler, we’ve broken it down into the following categories:
Tech
Consumers can purchase everything from a VPN service (ExpressVPN) to cloud storage space (Mega.nz) with the cryptocurrency. Microsoft, Wikipedia and AT&T also grace the list, having accepted Bitcoin as a payment method for some years now. Unsurprisingly, the gaming platform Twitch also features crypto payments (they disabled them and then brought them back). There is even a digital library in San Francisco providing the world with “universal access to all knowledge” that operates off of Bitcoin donations.
Sports
Tech you can understand, but sports? Yes, that’s right. A number of large sports clubs around the world have chosen to embrace the digital currency movement. In America, the most famous to do so are the Miami Dolphins and the Dallas Mavericks, while across the pond in the United Kingdom the following football clubs are all in: Tottenham Hotspur, Crystal Palace, Brighton & Hove Albion, Southampton, Leicester City, Newcastle United, and Cardiff City. S.L Benfica, one of the oldest and most popular sports clubs in Portugal, has also decided to accept Bitcoin for everything from merchandise to game tickets.
Retail
Most famously the American retailer dealing with home decor, Overstock, is one of the largest retailers to accept Bitcoin. Home Depot and Whole Foods also joined the ranks through the Winklevoss Flexa spending app ‘Spedn’ that allows for seamless crypto payments.
Then there are companies that provide a middle ground enabling you to purchase goods from stores that don’t necessarily accept the cryptocurrency directly. This includes Purse.io that is most famously used for Amazon purchase with Bitcoin, and Gyft, a company that sells gift cards for popular stores in exchange for crypto. Gyft can be used for everything from Starbucks to Sephora to iTunes.
Travel
You’d be surprised how many travel companies are now offering purchases with cryptocurrencies. One of the first to cross over was Latvia’s national airline, airBaltic, which announced in 2014 that they would be offering the payment option. Since then a number of leading travel companies including Expedia, CheapAir, and Destinia have followed suit. Alternatively, you could purchase a trip to space with Richard Branson’s Virgin Galactic. There is even a specially designed travel company catering solely to Bitcoin shoppers, Bitcoin.Travel.
Food
Another industry to embrace Bitcoin payments with a number of top fast food chains embracing the crypto life in various corners of the globe. Multiple Subways around the world, Pizza Hut in Venezuela, 40 international locations of Burger King, and KFC in Canada have all joined the forward driven club.
BTC Tapping Into The Future
And then of course just about anything in Japan. If you’re looking for goods to purchase with Bitcoin, you can usually see from an online stores’ homepage if it is an option, or in a brick-and-mortar store there will usually be QR code at the checkout counter indicating that Bitcoin is accepted there. If you’ve found that Bitcoin payments are definitely for you, buy, send and spend BTC directly from your Tap app. What can you buy with Bitcoin through your Tap app? Just about anything thanks to the seamless payments integration technology.

If you've been exploring the world of cryptocurrency beyond Bitcoin and Ethereum, you've probably heard of Sushi. No, not the Japanese dish – we're talking about a powerful player in the decentralised finance (DeFi) space that's been making waves since its dramatic entrance in 2020.
Sushi, or SushiSwap as the platform is called, burst onto the crypto scene with what many called a "vampire attack" on Uniswap, another popular decentralised exchange (DEX). This bold move involved attracting over a billion dollars of liquidity from its competitor in just a few days.
Today, SushiSwap stands as one of the leading decentralised exchanges in the crypto ecosystem, offering a suite of financial services that go well beyond simple token swapping. With its native SUSHI token, the platform has created an ecosystem that allows users to trade, earn, lend, borrow, and more – all without traditional financial intermediaries.
What makes Sushi truly stand out is how it's putting financial power back into the hands of regular users. By democratising access to sophisticated financial tools that were once only available to privileged institutions, Sushi is helping to create a more open, accessible financial system for everyone.
What is Sushi (SUSHI)?
At its core, Sushi is a DEX and DeFi protocol that allows users to trade cryptocurrencies directly with each other without any middlemen. Unlike centralised exchanges, there's no company controlling your funds or verifying your identity – it's just you, smart contracts, and the blockchain.
Think of SushiSwap as an online marketplace where instead of a company facilitating trades, everything runs on code. It's like if eBay operated without eBay the company – just buyers and sellers interacting through an automated system.
The relationship between SushiSwap and SUSHI is important to understand:
- SushiSwap is the platform – the actual decentralised exchange and suite of DeFi services
- SUSHI is the native token that powers the ecosystem – like owning a piece of the project
The Sushi ecosystem has evolved significantly since its launch, now offering a full menu of DeFi services:
- Token swapping (the basic exchange function)
- Liquidity providing (where users can earn fees)
- Yield farming (earning rewards by supporting the platform)
- Lending and borrowing
- Token launches
- NFT marketplace
- Cross-chain functionality (operating across multiple blockchains)
When compared to other DEXs like Uniswap and PancakeSwap, Sushi stands out for its community-first approach and wide range of features. While Uniswap pioneered the automated market maker model that Sushi uses, Sushi expanded on this foundation by adding more ways for users to participate and earn rewards.
And while PancakeSwap operates primarily on the Binance Smart Chain, Sushi has expanded to multiple blockchains, including Ethereum, Polygon, Avalanche, and more.
The history of Sushi
Sushi's history reads like a crypto soap opera – complete with controversy, drama, and unexpected twists. Grab the popcorn.
It all began in August 2020 when an anonymous developer going by the name "Chef Nomi" created SushiSwap as a fork (essentially a copy with modifications) of Uniswap's code. But Chef Nomi didn't just launch a competitor; they executed what became known as a "vampire attack" – a strategy to drain liquidity from Uniswap by offering better incentives.
Users who provided liquidity to Uniswap could stake their LP (liquidity provider) tokens on SushiSwap to earn SUSHI rewards. Then, in a coordinated event called "The Migration," over $1 billion in crypto assets moved from Uniswap to SushiSwap virtually overnight. The crypto community was stunned by the aggressive yet innovative approach.
But the drama was just beginning. Shortly after the successful migration, Chef Nomi suddenly converted a large amount of SUSHI tokens (worth about $14 million at the time) into Ethereum and withdrew it. The community viewed this as an "exit scam," and the price of SUSHI plummeted.
In a surprising turn of events, Sam Bankman-Fried, then-CEO of FTX (a major crypto exchange at the time), stepped in to take control of the project. Days later, Chef Nomi returned all the funds and apologised to the community.
Control of the project was then transferred to a multi-signature wallet controlled by several trusted community members, transitioning SushiSwap to true community governance. Since then, the protocol has seen steady development and expansion, including:
- Launch of Kashi lending platform (March 2021)
- Introduction of BentoBox, a yield-generating vault (Q1 2021)
- Expansion to multiple blockchains beyond Ethereum
- Release of Miso launchpad for new tokens
- Development of Shoyu, an NFT marketplace
Despite its tumultuous beginnings, Sushi managed to establish itself as a serious contender in the DeFi space through continuous innovation and a strong community focus.
How does SushiSwap work?
SushiSwap operates on a model called an automated market maker (AMM), which is fundamentally different from traditional exchanges. Here's how it works in simple terms:
Instead of matching buyers with sellers (the way stock exchanges work), SushiSwap uses liquidity pools – essentially big pots of cryptocurrencies that users can trade against. Imagine a vending machine that's always ready to exchange one token for another, rather than waiting to find someone who wants the opposite side of your trade.
These pools are created and maintained by liquidity providers – regular users who deposit pairs of tokens (like ETH and USDT) into the pools. In return for providing this liquidity, they earn fees from trades that happen in their pool.
When you want to swap tokens on SushiSwap, here's what happens:
- You select the tokens you want to exchange (for example, ETH for USDT)
- Smart contracts calculate the exchange rate based on the ratio of tokens in the relevant liquidity pool
- The more of one token you want, the more expensive it gets (this is called "slippage")
- A small fee (0.3% of the trade) is taken and distributed to liquidity providers
- The tokens are exchanged directly in your wallet
The beauty of this system is that it's all handled by smart contracts – self-executing code on the blockchain. There's no company processing your trade or holding your funds; it's all automated and trustless.
Of this 0.3% fee, 0.25% goes directly to liquidity providers in the pool, while the remaining 0.05% is converted to SUSHI tokens and distributed to SUSHI stakers. This creates a sustainable revenue model where active users earn from the platform's success.
Key features of the Sushi ecosystem
Sushi has evolved from a simple token exchange into a comprehensive DeFi ecosystem. Let's explore the main ingredients in Sushi's expanding menu:
SushiSwap DEX: The heart of the ecosystem is the decentralised exchange where users can swap virtually any ERC-20 token (and tokens on other supported blockchains). With competitive rates and deep liquidity across many trading pairs, it's the foundation of the Sushi experience.
Kashi: This lending and margin trading platform allows users to borrow assets against their crypto collateral. What makes Kashi unique is its isolated risk markets – meaning a problem in one lending market won't affect others, making it potentially safer than some competitors.
BentoBox: Think of this as a smart crypto savings account. BentoBox is a token vault that generates yield on deposited assets while they're waiting to be used in other Sushi products. It's like your money earning interest while sitting in your wallet, ready to use.
Onsen: This liquidity mining program incentivises users to provide liquidity for specific token pairs by offering additional SUSHI rewards. It's named after Japanese hot springs – places where people gather and relax, much like how Onsen gathers liquidity for the platform.
Miso: A launchpad for new tokens, Miso helps projects conduct token sales with various auction types. It's like Kickstarter for new crypto projects, helping them raise funds and distribute tokens fairly.
Shoyu: Sushi's NFT marketplace allows for the creation, buying, and selling of digital collectables. While newer than some competitors, it aims to offer lower fees and better integration with the rest of the Sushi ecosystem.
Cross-chain deployment: Unlike many DeFi protocols that only exist on Ethereum, Sushi has expanded to numerous blockchains including Polygon, Avalanche, Binance Smart Chain, Fantom, and more. This multi-chain approach helps users avoid Ethereum's sometimes high transaction fees while still accessing Sushi's services.
This diverse ecosystem makes Sushi a one-stop shop for many DeFi activities, allowing users to move seamlessly between trading, earning, lending, and more.
SUSHI tokenomics
The SUSHI token is the special sauce that brings the whole Sushi ecosystem together. Let's break down how it works:
Total supply: SUSHI has no maximum supply cap. New tokens are minted at a rate of 100 SUSHI per Ethereum block (roughly every 12 seconds), though this emission rate has been adjusted through governance votes over time.
Token utility: The SUSHI token serves several important functions:
- Governance: SUSHI holders can vote on proposals to change the protocol
- Fee sharing: When staked, SUSHI entitles holders to a portion of all trading fees
- Liquidity mining rewards: Users can earn SUSHI by providing liquidity
- Platform access: Some features may require SUSHI holdings or staking
Governance rights: Holding SUSHI means having a say in the future of the platform. Token holders can propose and vote on changes ranging from technical upgrades to treasury management and new feature development.
xSUSHI mechanism: When users stake their SUSHI tokens, they receive xSUSHI in return. This represents their share of the staking pool, which constantly grows as trading fees are added to it. When users unstake, they get their original SUSHI plus their portion of accumulated fees – making it a passive income opportunity.
Staking rewards: The current APY (Annual Percentage Yield) for staking SUSHI varies depending on platform volume and the number of stakers, but it has historically offered attractive returns compared to traditional finance.
Market performance: As with many cryptocurrencies, SUSHI has experienced significant price volatility since its launch. After reaching all-time highs during the 2021 bull market, the token has settled into a more stable trading range.
The tokenomics of SUSHI are designed to align the interests of users, liquidity providers, and token holders – when the platform succeeds, SUSHI holders benefit through increased value and fee sharing.
How to buy and sell SUSHI
Looking to get your hands on some SUSHI tokens? Here's how you can do it through the Tap app:
How to buy SUSHI on the Tap App:
- Download the Tap app from your device's app store
- Create an account and complete the required verification
- Fund your account using a supported payment method (bank transfer, card, etc.)
- Navigate to the crypto section and search for SUSHI
- Enter the amount you want to buy
- Review the transaction details and confirm your purchase
- Your SUSHI tokens will appear in your Tap wallet
How to sell SUSHI on the Tap App:
- Navigate to your SUSHI wallet in the app
- Select the Sell option
- Enter the amount you want to sell, and what currency you would like in return (crypto or fiat)
- Review and confirm the transaction details
- Your desired currency will appear in the relevant Tap wallet
Conclusion
Sushi has come a long way from its controversial beginnings to establish itself as a cornerstone of the DeFi ecosystem. What started as a fork of Uniswap has evolved into a comprehensive financial platform that offers trading, earning, lending, and more – all without traditional financial intermediaries.
By addressing one of the biggest pain points in DeFi – high Ethereum gas fees – through multi-chain deployment, Sushi makes decentralised finance more accessible to everyday users.
As with any cryptocurrency project, Sushi faces challenges and competition, but its innovative features, passionate community, and continuous development make it a project worth watching in the years to come.

Bitcoin and Ethereum dominate headlines, but they represent just one approach to distributed ledger technology. While most projects iterate on blockchain's foundational concepts, Hedera Hashgraph (HBAR) takes a different approach, pursuing an entirely different architectural philosophy.
The result is a network engineered for enterprise-grade performance - processing thousands of transactions per second with deterministic fees and minimal energy consumption. Where many blockchain networks struggle with the scalability trilemma, Hedera's hashgraph consensus mechanism offers a compelling alternative that doesn't sacrifice security for speed.
What distinguishes Hedera in practice is its enterprise adoption trajectory. Major corporations across finance, healthcare, and supply chain management have moved beyond pilot programs to production deployments. This isn't theoretical adoption - it's measurable network activity from organizations with serious compliance and performance requirements.
Hedera has positioned itself as one of the most corporate-friendly distributed ledger technologies (DLTs) available today. But how exactly does it work, and why does it stand apart from the blockchain crowd?
The Basics: What Is Hedera Hashgraph?
Launched in 2018, Hedera Hashgraph is a distributed ledger technology that offers a genuine alternative to blockchain architecture. Instead of organizing transactions into sequential blocks like a digital filing cabinet, Hedera uses a directed acyclic graph (DAG) structure called the hashgraph. Think of it more like a web of interconnected transactions.
This design allows multiple transactions to be processed in parallel rather than waiting in a single-file line. The result? Hedera can handle over 10,000 transactions per second (TPS) with finality in just a few seconds, while Bitcoin manages about 6–8 TPS and Ethereum handles 12–15 TPS.
At its core, Hedera is engineered to tackle three persistent challenges that have plagued distributed ledger technology:
- Transactions settle in seconds, not the minutes or hours you might wait with other networks. This makes it possible to build applications where timing actually counts.
- Scalability without the usual trade-offs, The network can handle thousands of transactions simultaneously without slowing down or getting expensive when things get busy. Most blockchains struggle with this balancing act.
- Energy use that makes sense, unlike networks that consume as much electricity as small countries, Hedera runs efficiently enough that companies don't have to justify massive energy bills to their boards.
How Hedera Works: Gossip and Virtual Voting
Hedera's performance stems from its unique consensus mechanism, which combines two clever innovations that work together like a well-orchestrated dance.
Instead of broadcasting every transaction to the entire network simultaneously (imagine shouting news in a crowded room), nodes "gossip" by randomly sharing information with a few neighbors. Those nodes then pass it along to their neighbors, creating a ripple effect. Over time, the entire network organically learns about every transaction without the communication overhead. That is known as the “gossip-about-gossip protocol”.
Virtual voting is where things get interesting: once all nodes have the same historical record of gossip, they can independently calculate how the network would vote on each transaction. No actual vote messages need to be sent across the network. The outcome is mathematically deterministic based on the gossip history, saving significant time and bandwidth.
Together, these methods achieve asynchronous Byzantine fault tolerance (aBFT), which represents one of the highest levels of security available in distributed systems. This means the network can reach consensus and continue operating even if up to one-third of nodes act maliciously or fail completely.
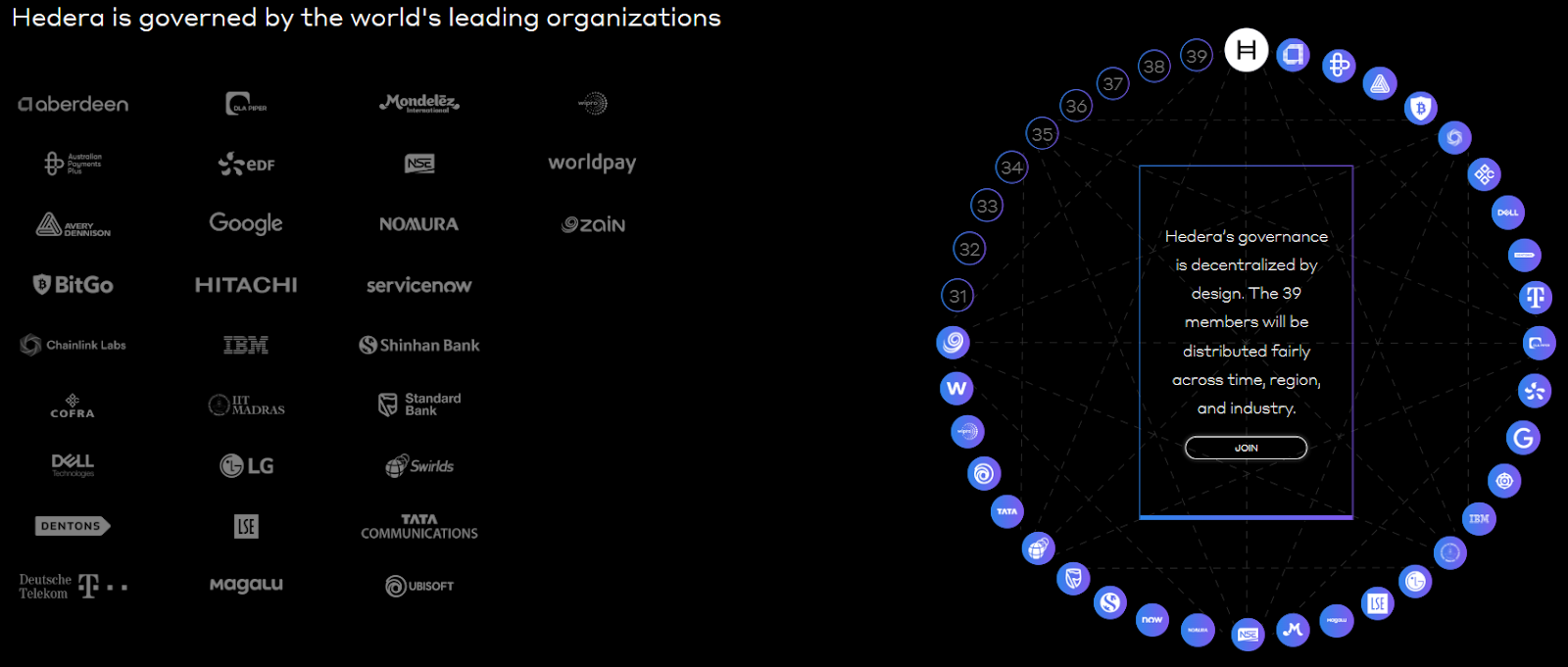
Governance: The Hedera Council
Perhaps the most controversial, and arguably the most distinctive, aspect of Hedera is its governance model. Instead of leaving critical network decisions to anonymous miners or distributed token holders, Hedera operates under a Governing Council of up to 39 well-known global organizations.
Current members include companies like Google, IBM, Dell, Boeing, Standard Bank, Ubisoft, and other established corporations. Each council member holds an equal vote on network decisions, including software upgrades, fee structures, and treasury management.
The rationale is straightforward: provide stability, accountability, and long-term strategic planning. However, this structure has sparked ongoing debate within the crypto community. Critics argue it reduces decentralization compared to blockchain networks where theoretically anyone can participate in governance, while supporters contend it offers the predictability that many enterprises require for serious adoption.
Key Services of Hedera
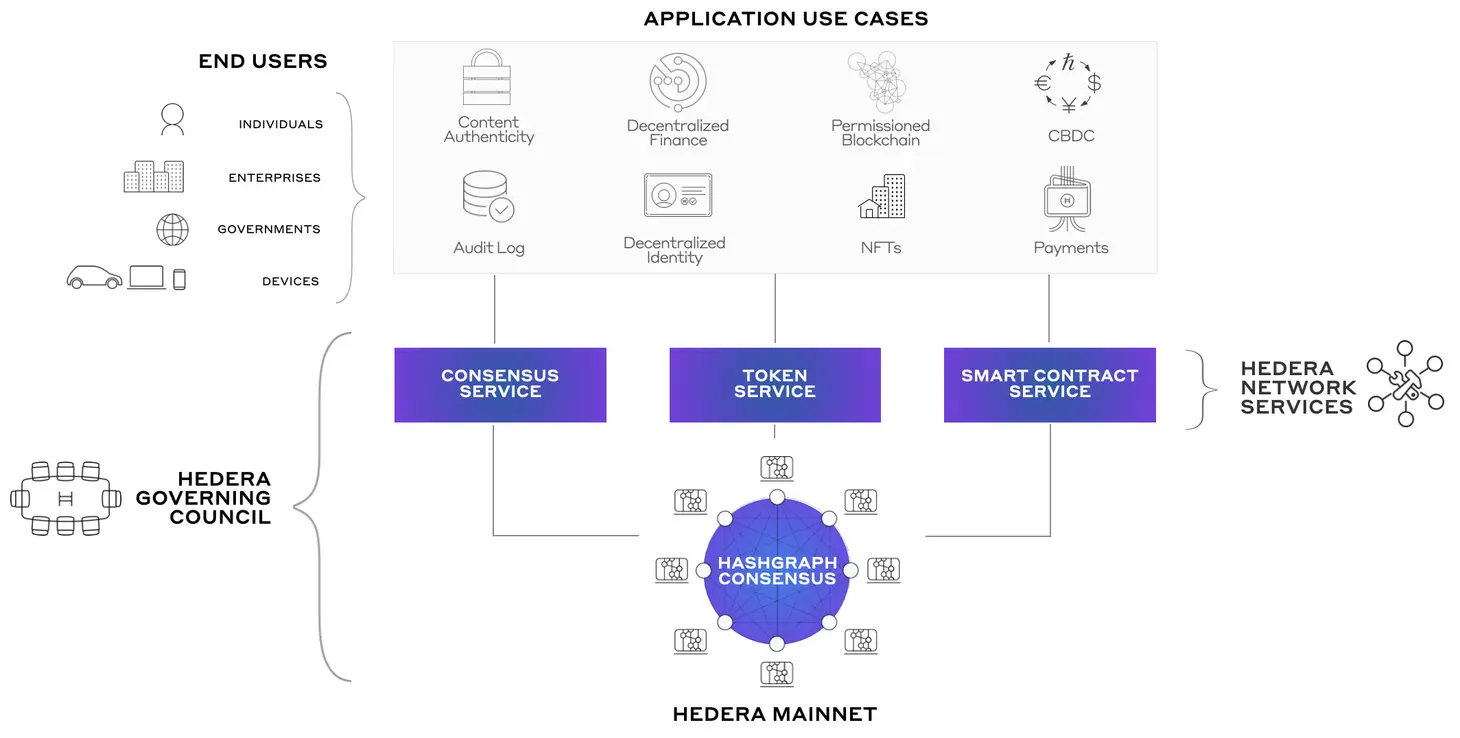
Hedera functions as more than just a payment network. The platform offers three core services that developers and enterprises can leverage to build decentralized applications:
Hedera Consensus Service (HCS): Provides secure, immutable logs of events and data. This proves particularly valuable for supply chain tracking, regulatory audits, and maintaining data integrity in heavily regulated industries like healthcare and finance.
Hedera Token Service (HTS): Enables the creation and management of various token types, including stablecoins, NFTs, and tokenized assets. Built-in features like account-level controls and compliance tools make it especially appealing for enterprises that need to meet regulatory requirements.
Hedera Smart Contract Service (HSCS): Supports Ethereum-compatible smart contracts, allowing developers to build DeFi applications, games, and automation tools while benefiting from Hedera's superior speed and substantially lower transaction fees.
Real-World Applications
Hedera's enterprise-focused approach has translated into practical implementations across multiple sectors:
- Finance: Standard Bank leverages Hedera's infrastructure for faster, more transparent cross-border payment processing.
- Supply chain: Companies like Suku and Avery Dennison use Hedera for product traceability and logistics management, providing end-to-end visibility.
- Healthcare: Safe Health Systems employs the network to securely log medical and clinical trial data while maintaining strict patient privacy standards.
- Gaming: Animoca Brands integrates Hedera's technology to create fair and tamper-proof in-game economies and digital asset management.
- Sustainability: Environmental organizations use Hedera's consensus service to track carbon credits and monitor environmental impact data with immutable records.
These implementations highlight Hedera's positioning as an enterprise-focused platform, creating a distinct contrast to networks that primarily serve DeFi protocols or retail trading activities.
Understanding HBAR: The Native Token
Like most distributed ledger technologies, Hedera operates with its own native cryptocurrency: HBAR. The token serves two fundamental purposes within the ecosystem:
- Network fuel: HBAR is required to pay transaction fees and access network services, including consensus operations, tokenization features, and smart contract execution.
- Network security: Node operators stake HBAR tokens to participate in consensus and help secure the network infrastructure.
One of Hedera's most practical advantages lies in its cost structure. A typical transaction costs approximately $0.0001, it’s economical enough to enable microtransactions and machine-to-machine payment scenarios that would be prohibitively expensive on other networks.
The total supply of HBAR is capped at 50 billion tokens. The distribution follows a controlled release schedule designed to avoid sudden market flooding while ensuring adequate liquidity for network operations.
How Hedera Compares to Other Networks
To understand Hedera's market position, it's helpful to consider how it stacks up against established blockchain models:
Proof-of-Work (PoW), exemplified by Bitcoin, is highly secure and battle-tested, but notoriously slow and energy-intensive.
Proof-of-Stake (PoS), used by Ethereum 2.0, is more energy-efficient than PoW, but can lead to wealth concentration among large token holders.
Lastly, Hedera Hashgraph uses gossip protocols and virtual voting to achieve speed, security, and efficiency simultaneously, while operating under corporate governance rather than anonymous network participants.
The trade-off is crystal-clear. Hedera prioritizes corporate trust, performance, and regulatory clarity, while accepting criticism that it may sacrifice some degree of decentralization compared to traditional blockchain networks.
The Challenges Ahead
Despite its technical strengths and enterprise adoption, Hedera faces some hurdles that could impact its long-term trajectory. The Governing Council model continues to raise questions about whether Hedera represents genuine decentralization or simply distributed corporate control, a debate that matters deeply to the broader crypto community's acceptance. Meanwhile, established networks like Solana, Avalanche, and Ethereum maintain their dominance over ecosystem development, making it challenging for Hedera to attract the vibrant developer communities that drive innovation.
The platform also faces an adoption challenge. While it excels in enterprise use cases, Hedera could broaden its appeal beyond corporate applications to achieve the kind of recognition that sustains long-term growth. Moreover, like all cryptocurrency projects, Hedera must navigate evolving regulatory frameworks across multiple jurisdictions, each with their own compliance requirements and restrictions.
Nevertheless, Hedera's focus on performance, enterprise-grade reliability, and regulatory compliance could provide resilience in certain market conditions where other projects would struggle to maintain institutional confidence.
HBAR ETF on the Horizon
Over the past several months, talk of a potential HBAR ETF has gained traction. An ETF would offer institutional and retail investors exposure to HBAR without needing to manage wallets, private keys, or direct custody. That kind of access lowers the entry-level barrier. Moreover, SEC approval of a Hedera ETF would imply a level of oversight, due diligence, and compliance that can help reduce perceived risks among cautious or regulated investors. It puts HBAR closer to the realm of mainstream finance instruments.
The U.S. Securities and Exchange Commission (SEC) recently pushed back the decision on the Canary HBAR ETF to November 8. The ETF was proposed by Nasdaq back in February; the SEC has delayed the decision twice already. Despite the most recent delay, however, market analysts remain optimistic. Bloomberg’s analysts, for instance, maintain a 90% likelihood of ETF approval in the near term.
The Future of Hedera
Hedera stands out in a crowded field by taking a completely different approach than most blockchain projects. Instead of following the usual playbook, they built something that actually works for businesses: fast transactions, costs you can predict, and energy usage that won't make your CFO cringe.
The real test isn't whether Hedera can keep doing what it's doing well. It's whether they can stay relevant as the whole distributed ledger world keeps evolving at breakneck speed. But here's the thing: while everyone else was busy trying to be the next Bitcoin, Hedera quietly built something that Fortune 500 companies actually want to use.
Whether that bet pays off long-term is anyone's guess. What's not up for debate is that they've proven there's more than one way to build a distributed ledger, and sometimes the road less traveled leads somewhere pretty interesting.

Let's Talk About Getting Your Crypto to Work While You Sleep
Remember when your grandparents bragged about their 2% savings account? Those days feel like ancient history now that crypto APY percentages are floating around that would make a traditional banker faint. But hold up, before you start dreaming about retiring next month on those sweet, sweet yields, let's dive into what APY actually means and why some of these numbers look like lottery tickets.
What the Is APY, Anyway?
Think of APY as compound interest on steroids. While your bank's savings account sits there earning dust, APY measures how much your money can actually grow in a year when interest keeps building on top of interest. The faucet of passive income is now open.
Here's a reality check: Park $1,000 in your bank at 5% simple interest, and you'll have a whopping $1,050 after a year. Yawn, boring… But that same money with 5% APY compounded monthly? You're looking at $1,051.16.
"Big deal, that's only a dollar!" you might say. But here's where it gets interesting. Over time, that compounding effect turns into a money snowball rolling down a mountain. The difference between simple interest and compound interest isn't just pennies; it's the difference between walking and taking a rocket ship.
APY vs. APR: The Sibling Rivalry You Need to Understand
Okay, confession time…even seasoned crypto folks mix these up. Here's your cheat sheet:
APY (Annual Percentage Yield): What you earn when you lend out your crypto. The higher, the better for your wallet.
APR (Annual Percentage Rate): What you pay when you borrow crypto. Lower is your friend here.
Think of it this way: APY is the cool cousin who brings you money, while APR is the one who always asks to borrow twenty bucks.
For a more detailed comparison, click here.
Where Does APY Show Up in Crypto?
- Crypto "Savings Accounts"
Some platforms let you deposit your tokens and watch them multiply. It's like putting your crypto to work at a job that actually pays decent wages. Your coins get lent out to traders who need them, and you get a cut of the action.
- Staking: Become a Network Validator
With Proof-of-Stake blockchains like Ethereum or Cardano, you can "stake" your tokens to help secure the network. Think of it as being a digital security guard who gets paid in crypto. The network stays safe, and you earn rewards. Win-win.
- Yield Farming: The Wild West of DeFi
This is where things get interesting, and a bit crazy. You provide liquidity to decentralized exchanges, and in return, you earn trading fees plus shiny new governance tokens. Early yield farmers sometimes see APYs that look like phone numbers, but don't get too excited; those rates have a habit of crashing back to earth.
- Lending Protocols: Become the Bank
Platforms like Aave and Compound let you play banker. You lend your tokens, borrowers pay interest, and you collect the proceeds. APY goes up when everyone wants to borrow your particular flavor of crypto, and down when the demand cools off.
Why Are Crypto APYs So High?
While your bank offers you a measly 0.5%, crypto platforms are throwing around eye-watering numbers like 10%, 50%, or even 1,000%+. Here's why:
Crypto traders will pay premium rates to short a token or execute complex arbitrage strategies. Supply and demand at its finest.
Hype for new projects also plays a role. Fresh projects often throw ridiculous APYs at users to attract liquidity. It's like a grand opening sale, but with more zeros.
Risk gets factored in. Let's be real, crypto can get risky at times. Higher returns compensate for the white-knuckle ride.
Finally, token Incentives can play a role too. Many of those eye-popping APYs come partially from project tokens that could moon... or crater. It's the crypto Russian roulette.
The Math Behind the Magic
Don't worry, we're not about to turn this into a calculus nightmare. The APY formula is actually pretty straightforward:
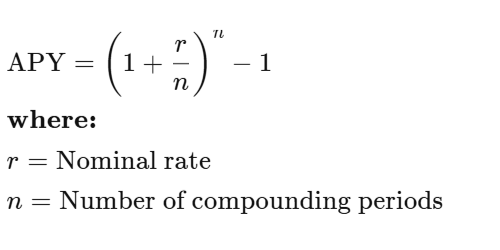
Example: 10% interest compounded monthly gives you about 10.47% APY. Compound it daily? You're looking at 10.52%. In crypto, some protocols compound every block, which is like compounding every few seconds. Your calculator might start smoking.
The Fine Print
Before you quit your day job and become a full-time yield farmer, let's talk about the risks that nobody likes to mention at crypto parties. First up is volatility. Sure, your APY might be 20%, but if your token's price drops 50%, you're still in the red. Math is cruel like that. Then there's impermanent loss, which sounds harmless but can eat into your gains faster than you can say "automated market maker" when you're providing liquidity and token prices start dancing around.
Don't forget about smart contract risk, either. DeFi protocols are basically computer programs holding billions of dollars, and if they break, funds can disappear into the digital ether without so much as a goodbye note. Platform risk is equally sobering. Remember Celsius? FTX? Sometimes the platforms themselves go belly-up, taking user funds with them like the Titanic.
Last but not least, there’s APY whiplash. That jaw-dropping 100% APY you bookmarked yesterday? It might be 15% today because crypto moves fast. Rates fluctuate based on demand, new competition, token economics, and sometimes just because the crypto gods felt like shaking things up.
What's a "Good" APY?
- Conservative. Sticking to blue-chip assets and reputable platforms for 3-8% APY. For the faint of heart.
- Moderate. Staking some altcoins or providing liquidity for 10-20% APY. There’s some excitement, but not heart-attack levels.
- High (YOLO). Chasing new DeFi projects for 50-100%+ APY. It’s worth keeping in mind there’s a non-zero chance your tokens might become expensive digital art.
Remember, if an APY looks too good to be true, it's probably attached to risks that would make a hedge fund manager nervous.
Crystal Ball Time: The Future of APY in Crypto
Here's where things get interesting. As crypto grows up, APYs are starting to act less like lottery tickets and more like actual financial products. Big institutions are getting into staking, regulators are paying attention, and the wild west is slowly becoming a proper town with actual roads.
It’s likely crypto will keep offering better yields than traditional finance. It's just that the 10,000% APY days are likely becoming a fond memory.
The Bottom Line
APY in crypto is the same mathematical concept your finance professor taught you, just dressed up in digital clothing and offering significantly better rates. Whether you're staking, lending, or yield farming, understanding APY helps you separate the wheat from the chaff and the legitimate opportunities from dubious schemes.
APY isn't a cheat code to infinite money. It's a tool that, when used wisely, can help your crypto actually work for you instead of just sitting in your wallet looking pretty. But like everything in crypto, it comes with risks that deserve respect and careful consideration.
It’s worth remembering the best APY in the world is worthless if the underlying project disappears into the digital sunset. Choose wisely, diversify smartly, and may your compounds be ever in your favor.
TAP'S NEWS AND UPDATES
What’s a Rich Text element?
What’s a Rich Text element?The rich text element allows you to create and format headings, paragraphs, blockquotes, images, and video all in one place instead of having to add and format them individually. Just double-click and easily create content.
The rich text element allows you to create and format headings, paragraphs, blockquotes, images, and video all in one place instead of having to add and format them individually. Just double-click and easily create content.Static and dynamic content editing
Static and dynamic content editingA rich text element can be used with static or dynamic content. For static content, just drop it into any page and begin editing. For dynamic content, add a rich text field to any collection and then connect a rich text element to that field in the settings panel. Voila!
A rich text element can be used with static or dynamic content. For static content, just drop it into any page and begin editing. For dynamic content, add a rich text field to any collection and then connect a rich text element to that field in the settings panel. Voila!How to customize formatting for each rich text
How to customize formatting for each rich textHeadings, paragraphs, blockquotes, figures, images, and figure captions can all be styled after a class is added to the rich text element using the "When inside of" nested selector system.
Headings, paragraphs, blockquotes, figures, images, and figure captions can all be styled after a class is added to the rich text element using the "When inside of" nested selector system.What’s a Rich Text element?
What’s a Rich Text element?The rich text element allows you to create and format headings, paragraphs, blockquotes, images, and video all in one place instead of having to add and format them individually. Just double-click and easily create content.
The rich text element allows you to create and format headings, paragraphs, blockquotes, images, and video all in one place instead of having to add and format them individually. Just double-click and easily create content.Static and dynamic content editing
Static and dynamic content editingA rich text element can be used with static or dynamic content. For static content, just drop it into any page and begin editing. For dynamic content, add a rich text field to any collection and then connect a rich text element to that field in the settings panel. Voila!
A rich text element can be used with static or dynamic content. For static content, just drop it into any page and begin editing. For dynamic content, add a rich text field to any collection and then connect a rich text element to that field in the settings panel. Voila!How to customize formatting for each rich text
How to customize formatting for each rich textHeadings, paragraphs, blockquotes, figures, images, and figure captions can all be styled after a class is added to the rich text element using the "When inside of" nested selector system.
Headings, paragraphs, blockquotes, figures, images, and figure captions can all be styled after a class is added to the rich text element using the "When inside of" nested selector system.What’s a Rich Text element?
What’s a Rich Text element?The rich text element allows you to create and format headings, paragraphs, blockquotes, images, and video all in one place instead of having to add and format them individually. Just double-click and easily create content.
The rich text element allows you to create and format headings, paragraphs, blockquotes, images, and video all in one place instead of having to add and format them individually. Just double-click and easily create content.Static and dynamic content editing
Static and dynamic content editingA rich text element can be used with static or dynamic content. For static content, just drop it into any page and begin editing. For dynamic content, add a rich text field to any collection and then connect a rich text element to that field in the settings panel. Voila!
A rich text element can be used with static or dynamic content. For static content, just drop it into any page and begin editing. For dynamic content, add a rich text field to any collection and then connect a rich text element to that field in the settings panel. Voila!How to customize formatting for each rich text
How to customize formatting for each rich textHeadings, paragraphs, blockquotes, figures, images, and figure captions can all be styled after a class is added to the rich text element using the "When inside of" nested selector system.
Headings, paragraphs, blockquotes, figures, images, and figure captions can all be styled after a class is added to the rich text element using the "When inside of" nested selector system.What’s a Rich Text element?
What’s a Rich Text element?The rich text element allows you to create and format headings, paragraphs, blockquotes, images, and video all in one place instead of having to add and format them individually. Just double-click and easily create content.
The rich text element allows you to create and format headings, paragraphs, blockquotes, images, and video all in one place instead of having to add and format them individually. Just double-click and easily create content.Static and dynamic content editing
Static and dynamic content editingA rich text element can be used with static or dynamic content. For static content, just drop it into any page and begin editing. For dynamic content, add a rich text field to any collection and then connect a rich text element to that field in the settings panel. Voila!
A rich text element can be used with static or dynamic content. For static content, just drop it into any page and begin editing. For dynamic content, add a rich text field to any collection and then connect a rich text element to that field in the settings panel. Voila!How to customize formatting for each rich text
How to customize formatting for each rich textHeadings, paragraphs, blockquotes, figures, images, and figure captions can all be styled after a class is added to the rich text element using the "When inside of" nested selector system.
Headings, paragraphs, blockquotes, figures, images, and figure captions can all be styled after a class is added to the rich text element using the "When inside of" nested selector system.Kickstart your financial journey
Ready to take the first step? Join forward-thinking traders and savvy money users. Unlock new possibilities and start your path to success today.
Get started


.webp)





.webp)